This is likely to be one of the most exciting things I ever write about while also being one of the most technically simple: On May 27, 2021 I “Hacked” DEF CON 29. More specifically, I was able to dump a list of the names, e-mail addresses, and tickets of anyone who had bought a ticket online. For a conference that hosts a large amount of people who value their anonymity, this is a pretty big deal. Fortunately this vulnerability was remediated extremely quickly and after some investigation done by the affected company, it was confirmed that I was the first person to access this data.
Before I go into details of the hack, I first need to give a shoutout to both The Dark Tangent (@thedarktangent) and Guest Manager (https://www.guestmanager.com/) for how quickly they addressed this issue. I initially reported the vulnerability to DT over Reddit, and despite having never talked to him before, he got back to me almost immediately. DT then reached out to Guest Manager, who was able to push out a fix in under 48 hours! To quote DT directly: “Guest Manager was great to work with and very responsive.” While it’s unfortunate that such a critical flaw was found in Guest Manager’s product, I commend them for their rapid remediation and cooperation.
The Hack
As I mentioned earlier, this is about as technically simple as it gets. On May 26 I went to purchase my own ticket online. The process was simple and standard: Add to cart, purchase ticket. No sign-up of any kind required. Moments later I received the confirmation e-mail with a link to view my order. Viewing my order presented me with the following:
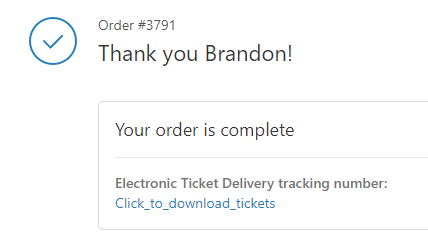
Just to make sure everything looked good, I went ahead and viewed my ticket. This sent me to: https://def-con-merchandise.guestmanager.com/viewer/orders/3791
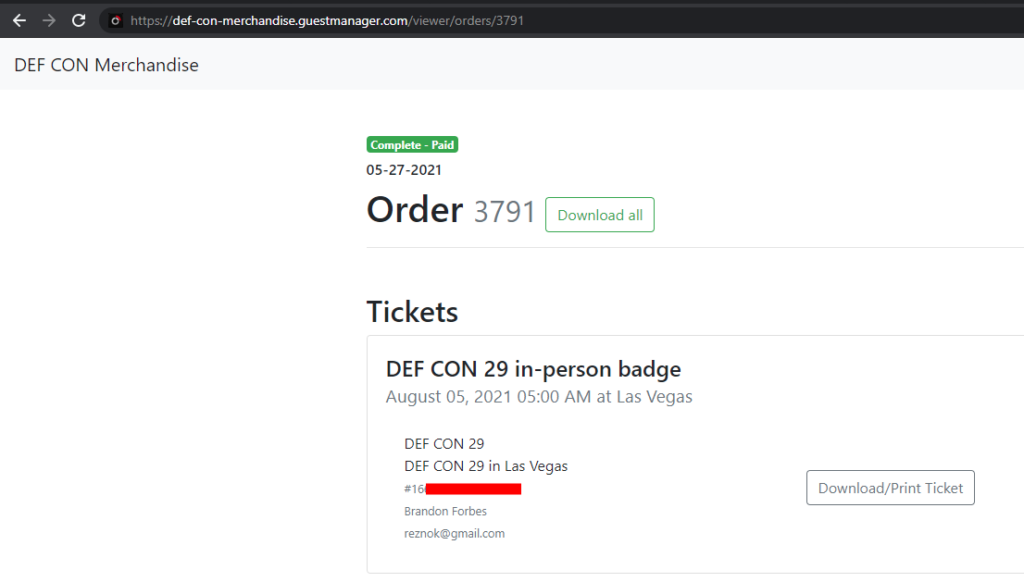
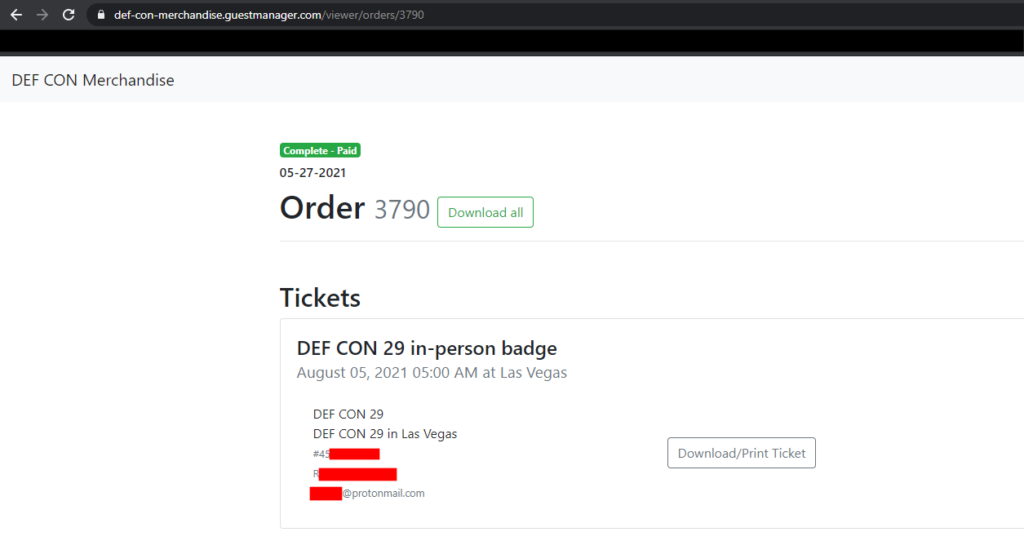
Great, there’s my ticket, my name, and my e-mail! (The redacted bit is my ticket barcode.) However, something bothered me at this point: As I mentioned before, I never had to sign up for anything and I was just given a link directly to my ticket information. So out of curiosity, I opened up an Incognito window and copy-pasted the URL to my order page, and to my surprise, it worked. Uh oh. No cookies, no password, no token, and there was my information for order 3791. Then I tried changing to URL to https://def-con-merchandise.guestmanager.com/viewer/orders/3790 to see if I could get order 3790, which also worked! And this time it was definitely not my information showing:
And just to triple check, I tried order 3789 which worked as well:
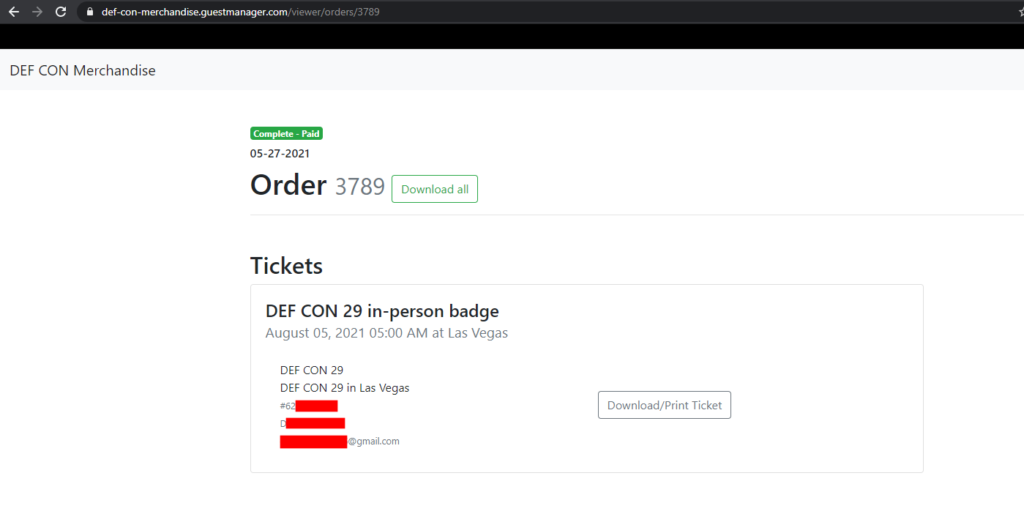
I retrieved approximately 5 different orders in total throughout my testing. I stopped at gathering enough evidence to prove the vulnerability, however a malicious attacker would be able to easily grab attendee information for every registration through the Guest Manager system.
What I had found was a very well known access control vulnerability known as IDOR (Insecure Direct Object Reference). To exploit this IDOR vulnerability, all an attacker needs to identify is how the order numbers are generated, which in this case was incrementally, and that no authentication is required. This exploit example is about as straight forward as web hacking gets, but even if an exploit is simple, it can still be highly impactful.
The Remediation
Guest Manager fixed their access control issue by adding access control to the order confirmation screen. If any users tried clicking the links above, they should (hopefully) have seen a “Not Authorized” error. Now, when users click the Click_to_download_tickets link in the e-mail, they end up being redirected to:
https://def-con-merchandise.guestmanager.com/viewer/orders/3791?token=[TOKEN]
Without that token, other users won’t be able to view the ticket details. This token appears to be related to an order number, since it is displayed after clicking the “View Your Order” button inside the confirmation e-mail. This button then sends users to the page with the “Click_to_download_tickets” link.
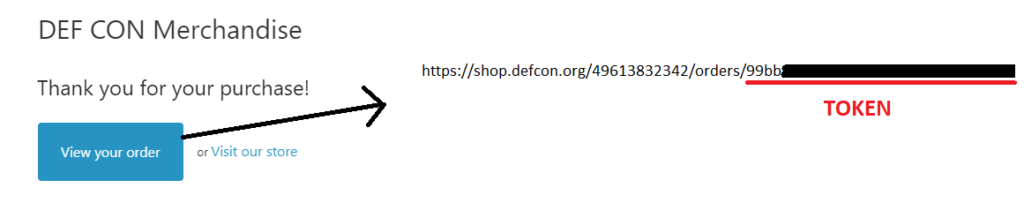
I do not (yet!) know how secure the generation of this token is, but at the very least, their current implementation is a lot better than it was before.
Timeline
- May 27, 2021 [03:14]: Reported vulnerability to /u/DTangent via Reddit
- May 27, 2021 [03:43]: DT acknowledges the vulnerability and reached out to Guest Manager
- May 28, 2021 [17:05]: DT informed me that Guest Manager has deployed a fix, but requested time before public disclosure
- June 18th: Public disclosure approved